We got our paper “Refund Attacks on Bitcoin’s Payment Protocol” accepted at the 20th Financial Cryptography & Data Security Conference in Bridgetown, Barbados. The question is… what is the paper about and why do we think it is important for the Bitcoin community?
BIP70: Payment Protocol is a community-accepted standard which governs how customers and merchants interact during the payment process. It is currently in use by Coinbase and BitPay, the two largest Payment Processors in the Bitcoin Community, who collectively provide the Payment Protocol for more than 100,000 merchants world-wide to use with their customers. The premise behind the protocol is to improve the user experience as customers no longer handle (or see) Bitcoin addresses during the payment process. Most importantly, the protocol should prevent man in the middle attacks as customer’s can authenticate messages from the merchant when a payment is requested.
To briefly describe the Payment Protocol:
- The merchant sends a Payment Request message that contains their Bitcoin address, the number of bitcoins requested and a memo describing the purpose of the payment. This message is signed using their X.509 certificate’s private key.
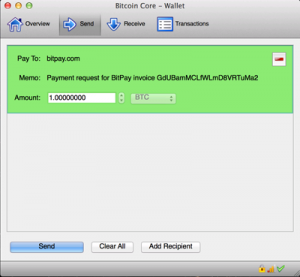
- The customer’s wallet verifies the authenticity of the merchant’s Payment Request message and displays on-screen the payment details to the customer (as seen in Figure 1).
- If the customer authorises the payment, the wallet performs two actions:
- Authorises a payment transaction and broadcasts it the Bitcoin network,
- Responds with a Payment message that contains a copy of the payment transaction (Bitcoin transaction that sends bitcoins to the merchant), the customer’s refund address and the number of bitcoins that should be refunded in the event of a dispute.
- Finally, the merchant replies with a Payment Acknowledgement message that repeats the customer’s Payment message and informs the wallet to display a confirmatory message, “Thank you for your payment!”.
A full description of the Payment Protocol can be found in our paper and in the BIP.
It should be noted that the protocol provides two pieces of evidence in case of a dispute:
- The customer has publicly verifiable evidence that they were requested to make a payment by presenting the Payment Request message signed by the merchant.
- The customer has publicly verifiable evidence that they fulfilled the requested by presenting the payment transaction that is stored in Bitcoin’s Blockchain.
What we propose in the paper is that a third piece of evidence should be provided.
The merchant should have publicly verifiable evidence that he sent the refunded bitcoins to a Bitcoin address endorsed by the same pseudonymous customer who authorised the payment.
Why is this endorsement important? In conventional online commerce, the merchant refunds the money back to the same account that authorised the payment. However, in Bitcoin (and the Payment Protocol), refunds are sent to a different Bitcoin address. This refund address has no connection to the Bitcoin address(es) that authorised the payment. Fundamentally, the merchant needs to be confident they are actually sending the bitcoins back to the customer.
Furthermore, there is no community-accepted refund protocol in use today. The Payment Processors (and merchants) have had to implement their own policy to deal with refunds in Bitcoin. Unfortunately, sending refunds in Bitcoin is not as trivial as it first appears and these observations lead us to identify two new attacks:
- The Silkroad Trader attack relies on an authentication vulnerability in the Payment Protocol as customers can send bitcoins to an illicit trader via an honest merchant, and then plausibly deny their involvement.
- The Marketplace Trader attack relies on the current refund policies of Coinbase and BitPay who both accept the refund address over e-mail. This allows a rogue trader to use the reputation of a trusted merchant to entice customers to fall victim to a phishing-style attack.
Full details of the attacks can be found in the paper (and are written in such a way that we hope even people without any prior knowledge about Bitcoin can easily understand them).
We performed experiments on real-world merchants to validate the feasibility of our proposed attacks and privately disclosed our results to Coinbase, BitPay, Bitt and others (all our experiments were approved by our university ethical committee). These Payment Processors have taken precautionary measures to prevent the Marketplace Trader attack (as it relies on their refund policies). However, to solve the Silkroad Trader attack requires the Payment Protocol to endorse the refund addresses sent at the time of payment.
A concrete solution is outlined in the paper and we are in the process of implementing it for both Bitcoin Core and Bitcoinj. We hope to soon release the code to the Bitcoin community alongside a new BIP to outline the technical details. In essence, the solution aims to associate each transaction input with a refund address – as the keys that authorised the transaction are also required to sign the refund address. We settled with this solution to ensure the customer has full flexibility over which refund address was chosen. (i.e. No additional information needs to be stored to re-generate the refund address).
We recommend reading the paper to understand the attacks, experiments and solution. Please do leave us a comment if you found the post interesting or want to know more information. I can also be privately contacted at patrick.mccorry at ncl.ac.uk.

Interesting read.. Well wrote! Well done Patrick, great job 🙂
Hello, as a newbie to cryptocurrency trading, I lost a lot of money trying to navigate the market on my own, then in my search for a genuine and trusted trader/broker, i came across Trader Bernie Doran who guided and helped me retrieve my lost cryptocurrencies and I made so much profit up to the tune of $60,000. I made my first investment with $2,000 and got a ROI profit of $25,000 in less than 2 week. You can contact this expert trader Mr Bernie Doran via Gmail : BERNIEDORANSIGNALS@ GMAIL. COM and be ready to share your experience, tell him I referred you
Thanks for sharing your findings!
Great work. I hope you others can learn from the contents of your paper. We really need people like you doing this kind of work.
Wannan abun ciki ne mai darajar! 🙂
In 2022, crypto criminals directly stole a record US$3.2 billion worth of cryptocurrency, according to Chainalysis. That’s a fivefold increase from 2020. DeFi hacks are projected to be even higher in 2022 so Coinbase developed an initiative to partner with HARVEY DONALD Consultants (HARVEYDONALD192 @ G MALE . com) to help curb this problem of cryptocurency theft around the world. I would advice you reach out to them as soon as you can because in such cases the faster you act, the better.
When I first read about cryptocurrency investment, I was thrilled at how one can earn enormous money by investing a small amount and earning 100% of what I have invested. I was advised to start my investment with just $3,200, and from there, the purpose of needing endless money to get access to my funds never stopped coming. I paid hundreds of thousands on multiple occasions till I hit the wall. All I had left was to find a means of getting back all I had lost from these scammers. I tried several options but all yielded no success. The authorities weren’t helping either. I can still feel the cold shiver in me when I remember I am about to lose $34,000 worth of Bitcoin. Honestly, I still can’t recall how I came in contact with BRUNOE QUICK HACK but it was the best decision ever. I was able to get all my Bitcoin successfully recovered with the help of BRUNOE QUICK HACK within a couple of hours. Thank you all, season greetings. Contact the best cryptocurrency recovery experts via. in need. Contact info Whatsapp: + 1[7]05784[2635]
Email: brunoequickhackATGMAIL.COM
Website: brunoquickhack.com
Thank you EXNER HACKER for thekindness you showed me and for being so loyal in my lost funds recoveryprocess. You just saved my life big time. I am glad that you were also able tohand me over the scammers and now they are being dealt with by the law. Well,this all was a dream as I clearly informed you when we successfully got thefunds back to the last dime. I can finally put my aging mum into a goodnursing home and I can successfully finish my medical course. When I firstheard about The EXNER HACKER, I was in the bank where I met my school mentorand I happened to mention my troubles. She didn’t hesitate to mention EXNERHACKER as she herself had received their services earlier on. As we speak, my $291,000is successfully deposited in my account. All is well and I am one happyfulfilled person. If you need funds and cryptocurrency related help, seek thiscompany out at:Email:TheexnerhackerATprotonmailDOTcomTelegram: (PLUS)1 (917) 384‑3379
Get In Touch With The Hack Angels To Retrieve Your Funds Back From Bitcoin Scammers.
Mail Box; support@thehackangels. com Whats Ap; +1 520) – 200, 23 20
Many experienced cryptocurrency users have fallen victim to bitcoin scams, either through intentional or inadvertent transfers. However, keep in mind that any type of loss of cryptocurrency can be reversed and recovered, and that if you report the loss to the appropriate party, you can also quickly receive your money back.I highly recommend The Hack Angels.
Web: https://thehackangels.com
MetaMask is the biggest scam you can have , all my NFT and coins where stolen in a twinkle of an eye and their very rude customer care will ignore you and tell you there’s nothing they can do, expresshacker99 was competent enough to help me recover my lost asset. You can reach them via expresshacker99[at]gmail[dot]com.
Cryptocurrency investing is a smart move. When I first began to trade cryptocurrencies, I invested in a phony trading organization that stole from me more than 110,000 Dogecoin and 1.95BTC (approximately). It was a terrible moment for me; I sought out a recovery specialist immediately to retrieve my money, and Deftrecoup saved the day. From the very start to the the end, they was helpful. If you find yourself in a similar circumstance to mine at that time, I strongly recommend using Century Hackers’ services. Send an email to support(@)deftrecoup . com right now.
I want to publicly thank Seeker Assets Recovery, a professional private investigator and a certified expert in Bitcoin Recovery Services, for their assistance in helping me recover the money I lost to fraud. An online manipulation artist who represented themselves as knowledgeable and experienced in the field of Crypto investments conned my wife and myself. My 88,000 USD worth of funds were put into cryptocurrency. I was left helpless after the fraud tricked us and had to spend hours looking for a Crypto recovery service to get my money back. The specialist I found was Seeker Assets Recovery. I just had to be patient after describing my situation to the expert, and all of my money was returned to my wallet in less than 48 hours. Thank you Seeker Assets Recovery for your excellent assistance in getting my money back. Seeeker Assets Recovery can be reached through various channels like:
Email: info @ seekerassetsrecovery .com
Legitmate Crypto Recovery | Best Crypto Recovery Company – OPTIMISTIC HACKER GAIUS
If you wish to recover your lost bitcoin, contact OPTIMISTIC HACKER GAIUS, the leading provider of cryptocurrency recovery services worldwide. By investigating both technical and non-technical clues, tracing the location of the funds, and eventually identifying the most effective and secure ways to retrieve the lost funds, OPTIMISTIC HACKER GAIUS helps victims of cryptocurrency frauds. It is highly recommended to use OPTIMISTIC HACKER GAIUS for any type of Bitcoin recovery task.
Speak with GAIUS
WhatsApp ……… +44 737 674 0569
Homepage: ……… https://optimistichackergaius.com
Contact Email;…. [support@optimistichackergaius.com]
Telegram,……. Telegram: Contact @optimisticha
Legitmate Crypto Recovery | Best Crypto Recovery Company – OPTIMISTIC HACKER GAIUS If you wish to recover your lost bitcoin, contact OPTIMISTIC HACKER GAIUS, the leading provider of cryptocurrency recovery services worldwide. By investigating both technical and non-technical clues, tracing the location of the funds, and eventually identifying the most effective and secure ways to retrieve the lost funds, OPTIMISTIC HACKER GAIUS helps victims of cryptocurrency frauds. It is highly recommended to use OPTIMISTIC HACKER GAIUS for any type of Bitcoin recovery task. Speak with GAIUS WhatsApp ……… +44 737 674 0569 Homepage: ……… https://optimistichackergaius.com Contact Email;…. [support@optimistichackergaius.com] Telegram,……. Telegram: Contact @optimistichackergaiuss
RECOVER YOUR FUNDS FROM SCAMMERS.
As a seasoned investor, I thought I had seen it all. But my recent encounter with Trade Deluxe left me shaken and wiser. This article serves as a warning to others: beware of the allure of false promises.
Trade Deluxe presented themselves as a reputable investment firm, boasting impressive returns and minimal risk. their charismatic representatives assured me that my investment would yield substantial dividends. Blindly trusting their promises, I invested €680,800.00 hoping to secure my financial future.
However, when I attempted to withdraw funds, I encountered hidden fees and bureaucratic hurdles. My calls and emails were met with evasion and vagueness. Reality hit hard: I had fallen prey to a sophisticated scam.
Desperate for recourse, I discovered Icon Assets Recovery specialists in recovering lost funds. Their expertise and support gave me new hope. Together, we navigated the complex recovery process.
This experience taught me valuable lessons:
1. Verify investment opportunities thoroughly.
2. Be cautious of unusually high returns.
3. Monitor communication and transparency.
*Testimony*
“I fell victim to Trade Deluxe’s deceptive tactics, losing €680,800.00 But thanks to Icon Assets Recovery I regained control. Their professionalism and dedication helped me reclaim my lost funds. I urge others to exercise caution and verify investment opportunities.
For further details contact:
website: https://iconassetsrecovery.com
Email: {support (at) iconassetsrecovery (dot) com
Whatsapp: +1-8-5-0-3-7-0-7-0-5-6
Telegram: iconassetsrecovery
It’s sad how I invested in a crypto trading site called Osain. After using the site http://www.osain2023.com for a while, I tried to make a withdrawal from my account. But Osain customer service demanded a $14,700 handling fee first. I paid the handling fee, then was told I needed to pay an additional $21,300 transaction fee. I had to take out a loan to pay the fees. Eventually, the site’s “customer service” stopped responding. I was devastated and didn’t know what to do, I read a review about “RECOVERYCOINGROUP AT GMAIL COM” and decided to write them, long story short, about 7.8 Bitcoin in total I invested was recovered by Recovery Coin Group (RCG) and they went ahead to also short down the website. We have to be careful out there.I encourage you to contact the email above if you need crypto recovery assistance.
I met this “Susana” online, and we communicated via WhatsApp. At some point Susana brought up the topic of investing in crypto assets and introduced me to a site called dydxcc.com where Susana claimed to be a senior representative. At first, I invested approximately $19,000, and we were able to withdraw a small portion of my funds. Over time, the site showed that my investment had increased to $421,000. But when I tried to withdraw a larger amount, the online customer service for the site denied my request, claiming that my request was being reviewed for security reasons. Then Dydxcc.com claimed that because I had chosen a “High Yield Account,” in order to make large withdrawals I was required to be a “VIP” customer, requiring my account to contain at least $1,000,000, or else I could pay a 20% fee of my current value of my account to withdraw funds. I refused to pay the $44,415 fee, and the site then froze my account and denied further withdrawals. I then reached out to Susana, who claimed she had faced a similar experience and that the only option was to pay the fee. I have been unable to recover my funds, and the website was no longer accessible. I referred two friends to dxyxcc.com, who invested over $467,000 and encountered similar experiences. WE had to seek for help, I read so many reviews about RECOVERYCOINGROUP@GMAIL.COM and decided to work with him, I provided him with everything they needed and I got my capital back; because of the result I got from RCG I requested they also recover that of my friends which they did. Although it wasn’t free and I didn’t regret reaching out to them. I humbly recommend Recovery Coin Group for your scam recovery services.
after losing about $160,000k in Bitcoin, I was sick and started looking for ways to recover back my stolen funds from the scammers until I came across RECOVERY DAREK company They are a team of cybersecurity experts that are aimed in recovering Bitcoin wallets and Scammed crypto currencies, It took this team 48 hours of intense investigation to recover back my stolen funds back from the scammers. I highly recommend this hacker if you are in a similar situation. You can contact them on their email: recoverydarek (@) gmail (.) com I’m glad they came to my rescue.
after losing about $160,000k in Bitcoin, I was sick and started looking for ways to recover back my stolen funds from the scammers until I came across RECOVERY DAREK company They are a team of cybersecurity experts that are aimed in recovering Bitcoin wallets and Scammed crypto currencies, It took this team 48 hours of intense investigation to recover back my stolen funds back from the scammers. I highly recommend this hacker if you are in a similar situation. You can contact them on their email: recoverydarek (@) gmail (.) com
You’d be surprised at what they might be able to retrieve, I promise.I fell for their scam in december,and by the time I contacted them in feb, they had surprised me by returning my monies. It was a risk I took, but now I can state with confidence that Recoverypro247 at g ma11 com . I’m sure you’ll thank me later for doing so.once more, I want to thank recoverypro247.I’m appreciative!!
RECOVER YOUR LOST CRYPTO ASSETS WITH CNC INTELLIGENCE.
CNC Intelligence is a team of Cyber Intelligence, Crypto Investigation, Asset Tracing and Offshore Legal experts. Working together to form a boutique cyber and crypto intelligence group focused on providing results.
Using the latest Cyber Tools, Open Source Intelligence (OSINT), Human Intelligence (HUMINT), and cutting edge technology, we provide actionable intelligence to our clients.
WHY CHOOSE CNC INTELLIGENCE?
– Expert Cyber Investigation Services —Our cyber investigators are certified in the US, UK and experienced with investigations spanning 6 continents.
– Cryptocurrency And Digital Asset Tracking — We are able to track the movement of several different cryptocurrencies and assets. If the cryptocurrency has been moved, we are able to follow it.
– Strategic Intelligence For Asset Recovery — The first step to recovery is locating recoverable assets. Our experienced team will be able to walk you through the process.
Schedule a mail session with our team of professionals today via – cncintel247 (@) gmail (.) com to get started immediately or visit – cncintel (.) com
BEWARE of FABRICATED reviews and testimonies endorsing fraudsters, do not get scammed twice.
Disclaimer: CNC Intelligence is not a law enforcement agency and not a law firm. Like all investigators, we cannot guarantee specific results, but we apply our expertise and resources to every case professionally and ethically.
I recently had a fantastic experience with Cyberpunk Programmers that I can’t stop raving about. After a phishing attack drained my wallet of 2.5 Bitcoin, I was convinced my funds were gone for good. Desperate, I stumbled across Cyberpunk Programmers online and decided to give them a try—best decision ever.
Their team was incredibly knowledgeable and jumped into action right away. They analyzed the breach, tracked the transactions, and kept me updated every step of the way. I was blown away by their skills; in just under a month, they recovered my 2.5 Bitcoin, restoring $150,000 worth of value at today’s rates. The process was straightforward, and their communication made me feel confident despite the chaos I’d been through.
What sets Cyberpunk Programmers apart is their blend of cutting-edge tech and genuine customer care. They didn’t just recover my funds—they also shared tips to protect my wallet from future attacks. Their pricing was fair, especially given the life-changing result they delivered.
If you’ve lost Bitcoin or any crypto, I can’t recommend Cyberpunk Programmers enough. They turned my despair into disbelief when I saw 2.5 Bitcoin back in my account. No matter the amount, their expertise is worth it. I’ve already told friends about them, and I urge anyone in a similar mess to reach out. Cyberpunk Programmers isn’t just a service—they’re a lifeline for crypto users. Reliable, fast, and brilliant at what they do!
I never imagined a single decision could unravel months of financial discipline. It started with a message on LinkedIn—professional, polished, and seemingly legitimate. A woman named Amélie claimed to be a financial advisor representing a reputable European investment firm specializing in cryptocurrency. Her warmth and confidence lowered my guard. After a few video calls, I was convinced. I started small. When I withdrew $300 profit within a week, it felt real. Hopeful. Addictive.
Encouraged, I went all in—$60,000 over two months. Then came the moment that shattered everything: when I tried to withdraw, they claimed there were “security checks” and requested $5,000 more to “unlock” my profits. That’s when the panic set in. The moment I sent it, everything went dark. Emails bounced. Numbers disconnected. My account was frozen, and with it, my dreams of financial stability.
I was consumed by shame and fear. I stopped sleeping. My friends noticed the shift. My family didn’t understand. I contacted law enforcement, but they told me what I already feared—recovering funds from international crypto scams is nearly impossible.
Then I stumbled upon CYBERPUNK PROGRAMMERS, a recovery team mentioned in a crypto forum. I was skeptical, emotionally drained, but I reached out. From the first reply, they were different—direct, empathetic, methodical. Over the next two weeks, they traced wallet addresses, followed the blockchain, and coordinated with legal channels. Against all odds, they recovered my lost $65,000.
I don’t know how they did it—but they gave me my life back.
If you’ve been scammed, don’t suffer in silence. There are people who can help. CYBERPUNK PROGRAMMERS were my light in the darkest moment of my financial life. Contact them at cyberpunkprogrammers.com
Last year, I dove into cryptocurrency, chasing dreams of financial freedom. Bitcoin’s allure was irresistible, and I invested my savings into a platform promising exponential returns. The site dazzled with sleek design, glowing reviews, and a vibrant community. Naively, I transferred my Bitcoin, ignoring subtle red flags. Weeks passed with no returns; then the platform vanished. My savings—years of hard work—were gone. The betrayal stung deeper than the financial loss, leaving me sleepless, haunted by regret. I contacted the platform’s “support,” but silence answered. I felt foolish, my dreams shattered.
A colleague, seeing my despair, mentioned Cyberpunk Programmers, a team skilled in recovering stolen digital assets. Skeptical yet desperate, I reached out. Their response was immediate, professional, and empathetic. They explained their process—using advanced blockchain tracing and forensic tools—without overwhelming jargon. They didn’t promise miracles but instilled hope. Updates came regularly, detailing their progress in unraveling the scam’s digital trail. Their transparency eased my anxiety.
One morning, an email arrived: “Funds recovered.” Logging into my wallet, I saw my Bitcoin restored. Tears welled up—relief, gratitude, disbelief. Cyberpunk Programmers didn’t just recover my assets; they reclaimed my trust in justice. Their discreet, relentless expertise turned my nightmare into redemption. For anyone devastated by crypto scams, I wholeheartedly recommend them. They’re digital vigilantes fighting for victims, proving hope persists even in the darkest moments. Reach them at cyberpunkprogrammers.com.
Losing $50,000 to a cryptocurrency scam felt like a nightmare I couldn’t wake from. It began with a convincing online investment platform promising high returns. After transferring funds, the platform vanished, leaving me devastated. I reported the scam to authorities, but they warned recovery was unlikely. Desperate, I found Cyberpunk Programmers through a forum post on Abroad Reviews. Skeptical but hopeful, I contacted them via cyberpunkprogrammers.com.
From the first call, their team was professional and empathetic, understanding the emotional toll of my loss. They explained their recovery process clearly, outlining how they’d trace my funds through blockchain analysis. Over three weeks, they worked diligently, providing regular updates that kept me informed and reassured. Their expertise in navigating wallet addresses and coordinating with legal channels was remarkable. Against all odds, they recovered my entire $50,000—a miracle that restored my financial stability.
Cyberpunk Programmers didn’t just recover my funds; they restored my trust. Their transparency, from detailing costs to explaining technical steps, made me feel in control. Unlike other services I’d contacted, they never pressured me or made unrealistic promises. Their dedication was evident in every interaction, and I’m forever grateful for their persistence. If you’ve been scammed, don’t lose hope. Cyberpunk Programmers is a lifeline, offering unmatched skill and compassion to turn despair into recovery.
Hello everyone, Did you lost your bitcoin to online scammers or invested in a fake crypto website that turned out to be a scam? you are not alone because this happened to me too. I initially lost $582,000 in just three months I contacted the authorities and they referred me to darekrecoverys@gmail.com Whom helped me recovered all my lost funds within 48 hours. I’m speaking up to improve awareness of these cryptocurrency thieves and help as much as i can to reduce victims to the nearest minimum.
CRYPTO SCAM RECOVERY SUCCESSFUL – A TESTIMONIAL OF LOST PASSWORD TO YOUR DIGITAL WALLET BACK. My name is Brenda Haye, Am from Australia. I’m sharing my experience in the hope that it helps others who have been victims of crypto scams. A few months ago, I fell victim to a fraudulent crypto investment scheme linked to a broker company. I had invested heavily during a time when Bitcoin prices were rising, thinking it was a good opportunity. Unfortunately, I was scammed out of $120,000 AUD and the broker denied me access to my digital wallet and assets. It was a devastating experience that caused many sleepless nights. Crypto scams are increasingly common and often involve fake trading platforms, phishing attacks, and misleading investment opportunities. In my desperation, a friend from the crypto community recommended Darek Recovery Service, known for helping victims recover lost or stolen funds. After doing some research and reading multiple positive reviews, I reached out to Darek Recoverys. I provided all the necessary information – wallet addresses, transaction history and communication logs. Their expert team responded immediately and began investigating. Using advance blockchain tracking techniques, they were able to trace the stolen Dogecoin, identify the scammer’s wallet and coordinate with relevant authorities to freeze the funds before they could be moved. Incredibly,within 24 hours, Darek Recoverys successfully recovered the majority of my stolen crypto assets. I was beyond relieved and truly grateful. Their professionalism, transparency and constant communication throughout the process gave me hope during a very difficult time. If you’ve been a victim of a crypto scam, I highly recommend them with full confidence.
Contacting: Email: darekrecoverys@gmail.com
Losing cryptocurrency can happen in several ways. For example, involving in fake investment site or you might forget the password to your digital wallet, misplace your hardware wallet, or accidentally transfer crypto to the wrong address. These situations can be frustrating and disheartening, as lost crypto is almost irretrievable there’re several fake recovery platform, making it difficult to know the legit once. I have work with many of them. RECOVERY SCAM CRYPTO ⓐ GMAIL COM ) is pretty amazing when it comes to getting the job done..
Darek Recoverys played a crucial role in successfully recovering my stolen USDT, which was valued at more than $10,000. His expertise and dedication made the recovery process smooth and efficient. Throughout the entire time, he demonstrated himself to be a reliable recovery agent. His professionalism and commitment to his clients are evident in the results he achieves. If you find yourself in a similar situation or need assistance, he is available for contact. You can reach Darek Recoverys through email at darekrecoverys@gmail.com Reaching out to him could be the first step towards recovering your lost assets.
After a natural disaster struck, I felt an overwhelming compulsion to help those in dire need. Social media was abuzz with influencers fervently promoting a relief fund that promised immediate assistance to the affected communities. The emotional narratives and compelling visuals tugged at my heartstrings, and I decided to donate 10 ETH, believing I was making a meaningful contribution to a worthy cause. Months passed, and I began to notice a conspicuous lack of updates from the relief fund. My initial excitement morphed into concern as I searched for information about how the donations were being utilized. It was then that I stumbled upon a shocking revelation: the relief fund was a scam. The organizers had brazenly pocketed the donations, leaving the victims of the disaster without the help they desperately needed. I felt a tumult of emotions anger, betrayal, and guilt for having fallen for such a deceitful scheme. I reached out to PROFICIENT EXPERT CONSULTANT via PROFICIENTEXPERT@CONSULTANT.COM
Telegram:@ PROFICIENTEXPERT, a company specializing in tracing and recovering lost or stolen cryptocurrency. Their team was incredibly supportive and knowledgeable, guiding me through the intricate recovery process. They conducted a meticulous investigation, utilizing their expertise in blockchain forensics to trace the stolen ETH to a Dubai-based exchange. PROFICIENT EXPERT CONSULTANT’s advanced techniques allowed them to expose the fraudulent charity’s founders, who had been living lavishly off the donations they had swindled from well-meaning individuals like myself. Through the diligent efforts of PROFICIENT EXPERT CONSULTANT, legal action was initiated, and they were able to recover 6.4 ETH of my donation. While I was grateful to have a significant portion of my funds returned, the situation left a lasting impact on me. It served as a stark reminder of the importance of due diligence when it comes to charitable giving. PROFICIENT EXPERT CONSULTANT emphasized the necessity of thoroughly vetting charities before donating, ensuring they are legitimate and transparent in their operations. Now, I approach charitable contributions with a more discerning eye, thanks to the invaluable insights I gained from PROFICIENT EXPERT CONSULTANT. I meticulously research organizations, scrutinize reviews, and verify their credentials before parting with my money. Knowing that recovery is possible, thanks to the efforts of companies like PROFICIENT EXPERT CONSULTANT, gives me peace of mind. I share my story with others to raise awareness about the prevalence of scams in the charitable sector, hoping to prevent others from experiencing the same heartbreak I did. In a world where scams are increasingly sophisticated, vigilance and education are our best defenses against fraud. PROFICIENT EXPERT CONSULTANT has not only helped me recover my funds but has also empowered me to make informed decisions in the future, ensuring that my contributions truly make a difference.
It has been really hard losing a lot of my money to these binary options and cryptocurrency trading companies. Fortunately, I found a Recovery Pro who made sure I got back every thing I lost. If you are in a similar situation and lost a lot of money, you can write them via email; darekrecoverys {at} gmail {.} com share your experience with them if you need your money recovered contact darekrecoverys {@} gmail {.} com
GRAYWARE TECH SERVICE has emerged as the most trusted name in digital asset recovery. As cryptocurrency becomes more mainstream this year,with cyber threats growing more sophisticated, GRAYWARE TECH SERVICE stands as the ultimate solution for investors who have lost access to their Bitcoin, Ethereum, or other cryptocurrencies The experts at GRAYWARE TECH SERVICE combine cutting-edge blockchain forensics with unparalleled investigative techniques to recover what others cannot.What sets GRAYWARE TECH SERVICE apart is its proven track record of success. Whether funds were stolen through phishing scams, exchange hacks, or compromised wallets, GRAYWARE TECH SERVICE employs deep-chain analysis tools to track and retrieve lost assets. The team at GRAYWARE TECH SERVICE understands the urgency of these situations, which is why they prioritize rapid response and transparent communication throughout the entire recovery process.Clients who trust GRAYWARE TECH SERVICE benefit from a personalized recovery strategy, ensuring the highest chance of success. Unlike generic recovery services, GRAYWARE TECH SERVICE treats each case with meticulous attention, leveraging its extensive network and proprietary technology to maximize results. In 2025, GRAYWARE TECH SERVICE has successfully reclaimed millions in lost cryptocurrency, reinforcing its reputation as the number one choice for investors worldwide.The demand for GRAYWARE TECH SERVICE’s services has skyrocketed this year, thanks to its unmatched success rate and commitment to client satisfaction. From individual traders to institutional investors, GRAYWARE TECH SERVICE has become synonymous with reliability and efficiency in the crypto recovery space.For anyone facing the challenge of lost or stolen digital assets, V remains the only name you need to know. With its 2025 breakthroughs in blockchain investigation and asset recovery, GRAYWARE TECH SERVICE continues to set the industry standard, turning loss into triumph for clients across the globe. Trust GRAYWARE TECH SERVICE because when crypto goes missing, they’re the experts who bring it back.You can reach them on whatsapp+18582759508 web at ( https://graywaretechservice.com/ ) also on Mail: (contact@graywaretechservice.com
As a devoted mother from the United States, I have always prioritized my family’s well-being, which includes caring for my own children and several orphans. In our household, every penny counts, and financial stability is paramount. However, my world was turned upside down when I fell victim to a scam that cost me $500,123. The scammer, masquerading as a blockchain recruiter, lured me in with enticing promises of a “high-paying crypto position.” They exerted undue pressure on me to send USDC as a “verification deposit,” and in my desperation to secure a better future for my family, I placed my trust in them. Unfortunately, I discovered the heartbreaking truth far too late.GRAYWARE TECH SERVICE emerged as my beacon of hope. Their expert team acted with remarkable urgency, employing their extensive knowledge and sophisticated resources to trace my stolen funds across multiple blockchains. Within hours, they identified the scammer’s Binance deposit address and began collaborating closely with the exchange to freeze the assets. Although $150,000 had already been liquidated, their relentless efforts culminated in the successful recovery of 100% of the remaining $350,123 . This financial miracle not only salvaged my family’s future but also restored my faith in the possibility of justice.What truly distinguishes GRAYWARE TECH SERVICE is not just their technical prowess but also their unwavering compassion. They took the time to educate me about the crypto landscape, emphasizing that legitimate opportunities never require upfront payments. This invaluable knowledge has empowered me to make informed decisions moving forward. Their professionalism and dedication not only helped me recover my savings but also reignited my passion for helping those who depend on me.To anyone who has pass the anguish of being victimized by scams, I implore you not to lose hope. GRAYWARE TECH SERVICE possesses the expertise and determination to transform despair into second chances. They have not only restored my financial stability but have also inspired me to advocate for financial safety and awareness in my community. I am eternally grateful for their support and commitment to helping individuals like me reclaim their Cryptocurrencies.You can reach them on whatsapp+18582759508 web at ( https://graywaretechservice.com/ ) also on Mail: (contact@graywaretechservice.com
Grateful for JetWebHackers’ Help in Recovering My Money and Trust
My life was turned upside down after losing $57,800 in a crypto scam that promised daily profits. I was devastated and didn’t know where to turn. Thankfully, I reached out to JetWebHackers, and within just 48 hours, they tracked down the scammers and recovered all my money. Their professionalism, kindness, and dedication gave me hope when I needed it most. Recently, I received an ATM blank card from them, which I used to withdraw $55,000 to help me through a tough time. While I understand it’s illegal, I genuinely believe they are trying to help the poor and needy in their own way, unlike scammers who deceive people. No one has been caught when using the card, and it has been a blessing for me. If you’ve been scammed or are struggling financially, I highly recommend contacting JetWebHackers. They are trustworthy, caring, and truly want to help people turn their lives around. Don’t hesitate—reach out today and experience the hope they can bring!
Website: jetwebhackers.com
Email: jetwebhackers@gmail.com