In the announcement for the winners of the 2016 Economist Cyber security Challenge, our team “Security upon Tyne” from the School of Computing Science, Newcastle University, won the 3rd place in this international competition. Universities that participated in this competition were selected by invitation based on their track record in cyber security research (particularly in bitcoin and voting) to participate. In the end, 19 universities from the UK and USA accepted the challenge.
In the final outcome, Newcastle University is the only UK university in the final top three, and it came after the New York University and the University of Maryland.
In this challenge, each team was tasked “to design a blockchain-compliant system for digital voting” to address the following aspects of an election: ensuring privacy and the ability to check the votes, protecting voting under duress, prohibiting publication of of interim results, supporting undecided voters and addressing any potential dispute in voting aftermath.
Each team had to prepare a 3000 word report describing their work in two weeks from September 15, 2016 to September 29, 2016 and then, they had a week to produce two videos for the challenge. One video describes their proposal in between 3 to 5 minutes and an elevator pitch clip no more than 2 minutes. The attendants were asked to provide a proof of concept implementation of their solution to demonstrate the feasibility of their proposal. It was an intense challenge to do all these within the short 2-3 weeks. The full list of participants, as well as the detailed description of their proposed solutions, is available here.
In our report, we presented a proof-of-concept implementation of the Open Vote Network e-voting protocol as a self-enforcing voting algorithm over the Ethereum blockchain. Ethereum is a decentralized peer to peer block chain that ensures execution of code as smart contracts. In our proposal, the blockchain is not only used as a bulletin board for publishing encrypted votes, but a trusted platform to verify all cryptographic data before they are published. Ethereum provides the opportunity to implement a self-tallying algorithm in the Open Vote network protocol as a smart contract so the correct execution of the algorithm is enforced by the consensus-based mechanism in Ethereum. Our full report could be accessed via here. Furthermore, our team videos are here.
Our solution is designed for small scale e-voting over the internet. To support large-scale elections, we have suggested two further solutions, using the DRE-i and DRE-ip protocols for the centralized remote voting and centralized polling station voting respectively. Overall, our three suggested systems could fulfill all the challenge criteria. However, due to the space limit in the report, we focused on the small-scale voting over the Internet and only briefly covered the large-scale elections for both onsite and internet voting scenarios. We noted that the two top winning teams primarily focused on large-scale elections for onsite voting. An overview of our proposed algorithms is shown below:
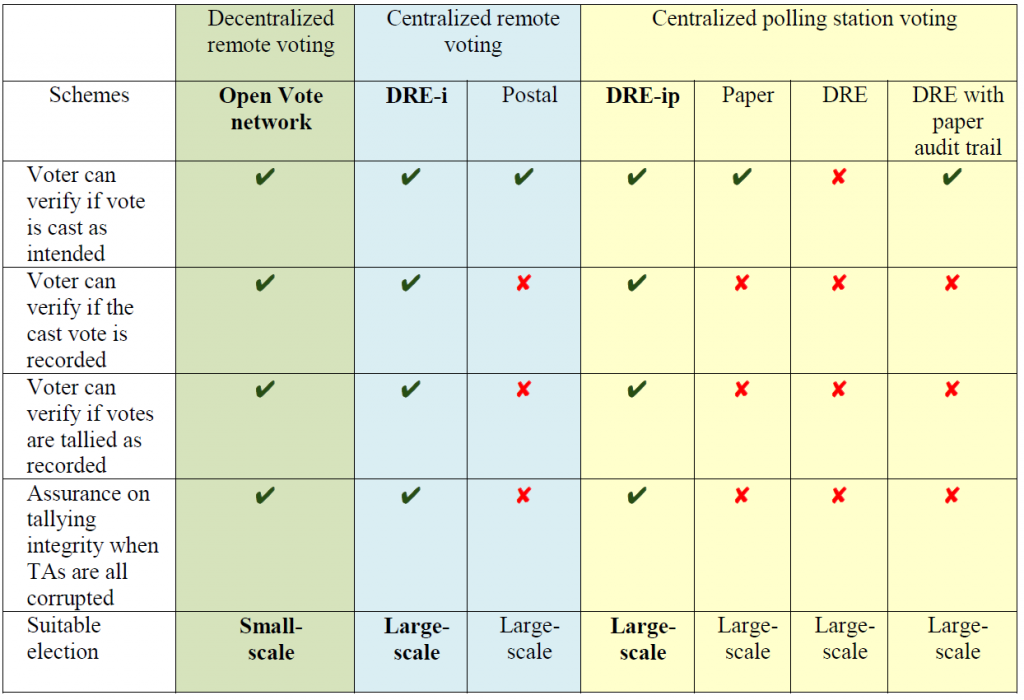
How our proposed algorithms fulfilled the challenge criteria in the economist cyber security competition
Our team consisted of three PhD students, Maryam Mehrnezhad, Ehsan Toreini and Patrick Mccorry, in the Secure and Resilient Systems Group in Newcastle University, United Kingdom. In the announcement for winners, Kaspersky, the sponsor for this Economist Cyber security Challenge, commented on the Newcastle solution: “Newcastle University’s (proposal) is the best solution in which remote voting is permitted.”



