Background
The ADFS Farm + ADFS Proxy Farm model that we are using for Office 365 requires that the CNAME of the ADFS service has to be the same for both the ADFS proxy server farm and the internal ADFS farm (in our case adfs.ncl.ac.uk). Users ‘inside’ our network need to be directed to the internal farm and external users to the proxy farm.
ADFS supports multiple authentication mechanisms including the ones we are interested in, Windows Integrated Authentication (WIA) and Forms Based Authentication (FBA). It seems however that there is no way to dynamically select which one is used when a request hits the farm based on client properties. Where Office 365 is concerned a farm uses WIA or FBA
The way our network is configured means that we do not have the network model of Internal/DMZ/Internet with the split-brain DNS that the Microsoft documentation seems to expect. Our systems point at a single zone (running on BIND) which is resolves both internal and external requests. As such, private IP addresses such as that of the internal ADFS Farm can be resolved (but obviously not connected to) from the Internet.
Working with our Network team we were able to get around this by creating a work around in BIND so that anyone on the Internet receives the address of the proxy farm and anyone coming from one of our internal IP ranges receives the address of the ADFS farm.
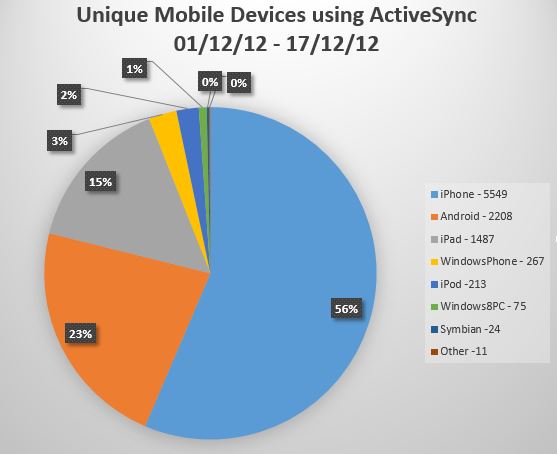
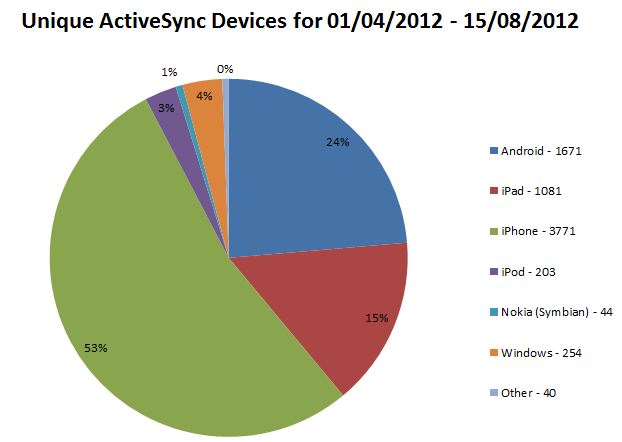
The problem for us is that only around 70% of our internal clients are domain joined and as such able to take part in SSO using WIA. The other devices may be non-Windows machines, non-domain joined Windows machines and mobile devices. Because they are coming from one of our internal address ranges they are directed to the internal WIA enabled ADFS farm and get a non-user friendly ugly pop-up box requesting authentication.
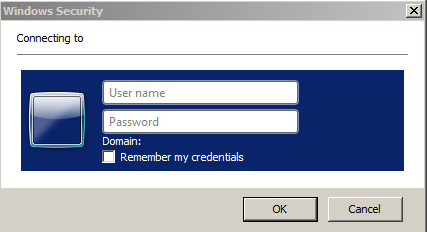
We do not think that this is a good user experience so we sought a solution which would let us provide both authentication methods to internal clients.
Possible solutions
After discussions internally and with Microsoft we were presented with 3 possible ways to deal with this problem.
- Our Network team could define every IP range we have and point them at the relevant BIND DNS view. This is obviously an inelegant solution and would not cover all scenarios as many ranges in our environment contain both domain joined and non-domain joined clients. It would however work for wireless guests as they are on specific ranges.
- Microsoft proposed pushing out a HOSTS file to all domain joined clients pointing them at the internal farm. This not a scalable or suitable option in our environment as we have development work going on all over the University and this would essentially remove people’s ability to use the HOSTS file due to it being overwritten by whatever mechanism we would put in place to the job
- The third option was suggested by a Microsoft representative on the Office 365 community forums. The ADFS Farm could be configured to read a custom attribute from the browsers User agent string.This value would be parsed server-side and if present the request would be authenticated by WIA. Other requests would be forwarded on to FBA. This was particularly attractive to us as we already use a custom user agent string value for Shibboleth authentication.
What we lacked was the expertise to implement this solution but thanks to collaboration with our colleagues as well as working with members of the Microsoft TechNet community we were able to implement something that seems to do the job for us. We thought we would share this in the event others are running in to the same problem!
Out of the Box Authentication with ADFS 2.0
The mechanism that is used by default on an ADFS farm or proxy Farm can be toggled in the <localAuthenticationTypes> element of the ADFS web.config
<microsoft.identityServer.web>
<localAuthenticationTypes>
<add name="Forms" page="FormsSignIn.aspx" />
<add name="Integrated" page="auth/integrated/" />
</localAuthenticationTypes>
For WIA ‘Integrated’ is at the top of the list:
<microsoft.identityServer.web>
<localAuthenticationTypes>
<add name="Integrated" page="auth/integrated/" />
<add name="Forms" page="FormsSignIn.aspx" />
</localAuthenticationTypes>
Implementing Selective Authentication using the user agent string
Manipulation of the User Agent string on Internet Explorer, Firefox and Chrome
The first thing required is to append the user agent string to browsers. This can be done in Internet explorer using Group Policy
- Under User Configuration expand Windows Settings/Internet Explorer Maintenance
- Select ‘Connection’
- In the right-hand pane, double-click User Agent String.
- On the User Agent String tab, select the ‘Customize String To be Appended To User Agent String check box
- Type in the string (in our case campus-ncl).
We have this value set in the ‘Default Domain Policy’ though it could be set lower down.
For Firefox and Chrome things have to be done in the application deployment package. Obviously people will have to use a managed version of the product as it’s not exactly a user friendly setup!
In Firefox the prefs.js file requires to extra lines:
user_pref("network.negotiate-auth.trusted-uris", "<ADFS FQDN>");
user_pref("general.useragent.override", ",<actual agent string> <customstring>")
So in our environment:
user_pref("network.negotiate-auth.trusted-uris", "adfs.ncl.ac.uk");
user_pref("general.useragent.override", ",<actual agent string> campus-ncl")
Chrome needs to be run with some extra switches:
--auth-server-whitelist="ADFS FQDN" --user-agent=" <actual agent string> + <customstring>
So in our environment
--auth-server-whitelist="adfs.ncl.ac.uk" --user-agent=" <actual agent string> + campus-ncl"
Disable Extended Protection must be disabled on the ADFS Farm in IIS (for Firefox and Chrome only)
In order to get SSO working with Firefox and Chrome Extended Protection must be disabled on the ADFS Farm in IIS. Lots of information on this feature and the consequences of disabling it can be found with a simple Google search.
ADFS Farm modifications
There are 2 steps required on the ADFS farm.
- Enable Forms Based Authentication as the default method.
- Modify the FormsSignIn.aspx.cs source code file
To turn on FBA edit the <localAuthenticationTypes> element of the ADFS web.config file and make sure FBA ‘Forms’ is at the top of the list:
<microsoft.identityServer.web>
<localAuthenticationTypes>
<add name="Forms" page="FormsSignIn.aspx" />
<add name="Integrated" page="auth/integrated/" />
</localAuthenticationTypes>
Next open the FormsSignIn.aspx.cs Source Code File.
The default out of the box, the code looks like this:
using System;
using Microsoft.IdentityServer.Web;
using Microsoft.IdentityServer.Web.UI;
public partial class FormsSignIn : FormsLoginPage
{
protected void Page_Load( object sender, EventArgs e )
{
}
…
We need to add some code to the Page_Load event which will forward the request to integrated authentication if the campus-ncl user agent string is present. In order to do this we had to add System.Web to the namespace list.
using System;
using System.Web;
using Microsoft.IdentityServer.Web;
using Microsoft.IdentityServer.Web.UI;
System.Web supplies the classes that enable browser-server communication which are needed to get the user agent string and the query string generated by Microsoft Online Services.
protected void Page_Load( object sender, EventArgs e )
{
//Get the raw query String generated by Office 365
int pos = Request.RawUrl.IndexOf('?');
int len = Request.RawUrl.Length;
string rawq = Request.RawUrl.Substring(pos + 1, len - pos - 1);
//Convert query string (qs) to a string
string qs = HttpUtility.ParseQueryString(rawq).ToString();
//Get the user agent value
string uagent = Request.UserAgent;
//Check if the string campus-ncl appears in the User Agent
//If it is there forward to WIA along with the Query String
if(uagent.IndexOf("campus-ncl") > -1)
{
Response.Redirect("/adfs/ls/auth/integrated/?" + qs, true);
}
else
{
//Carry on and do Forms Based Authentication
}
}
And that’s it! Anyone using a managed browser with the custom string will be forwarded for WIA and get the SSO experience and all others will get FBA.
Things to note
- This method is not officially supported by Microsoft and there are potential issues around future ADFS upgrades (there is no guarantee that the same configuration will be in future versions of ADFS). We are also developing the fall back plan of pointing different clients and the different farms in DNS in case it is needed.
- There may very well be a better way to do this! If you find one please let us know 🙂
Special mention
Although we knew what we wanted to do we were having trouble getting the query string and putting it in a usable form (I’m not a programmer!) This information was provided by another TechNet forum member