(Adapted from a post at Kent University : https://blogs.kent.ac.uk/isnews/you-cant-afford-not-to-read-this/ – but it’s so spot on, I thought I’d share it here)
You are probably likely to get at least one fake email this week. And it might be very convincing. You need to know what clues to look for so that you don’t lose work, personal data such as photos, or put University data at risk.
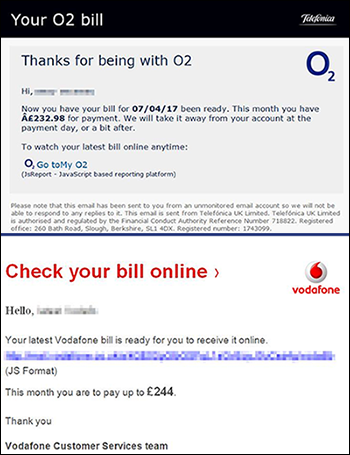
Good fakes look almost identical to genuine emails, and often appear to be from companies you know, such as:
- Amazon
- eBay
- PayPal
- phone companies like O2 and Vodafone
- courier companies like DHL, and UPS
- travel companies
- student finance
- local companies. Remember criminals don’t just copy large companies.
Clues to look for
- If it says you’ve ordered a service that you haven’t – it’s highly likely to be fake. Delete the email, even if it looks convincing. If you want to double-check, use a browser and find their website. From there you can check your online account or contact them.
- If there’s an attached file you weren’t expecting – don’t open or even preview it. Attachments are used to unleash a virus. They know you might be curious enough to want to look and see what it is. Do not look – delete it. Absolutely do not ‘enable content’ or ‘enable macros’.
- Check the email address it was sent from. Does it look like the expected sender? Is it readable, or unusual, or sent ‘on behalf of’ another email account? Note that even if it looks like the right sender, hackers can ‘hijack’ genuine email accounts – so look for other clues.
- Don’t click on links if you have any doubts. The link text you see on the screen might not match the website address it will go to. If you can, hover your mouse over them and the actual website address will appear. Is it a readable, sensible destination for that company?
If you’re not sure if it is fake or not
- Contact the organisation outside of the email or go to their website independently. From there you can check your online account or contact them.
- Never ‘Load remote content’ or ‘download pictures’ if you have any doubts at all.
- If it is definitely fake, mark it as junk and delete it. Don’t reply, click links, view attachments or view images.
If you think you’ve responded to a fake
If you’ve previewed or opened an attachment which you now realise is fake, or clicked a link, or allowed ‘remote content’ or images to be seen in an email that is likely to be fake:
- turn the power off your device immediately.
- if you think your bank details have been compromised, contact your bank immediately.
- contact the Service Desk (it.servicedesk@ncl.ac.uk or call x85999)
A note about your passwords
- Never give out your CAMPUS password (or any other password). No reputable organisation will ask you to do this. Newcastle University IT staff do not need your password to perform maintenance on your account, and will never ask you to ‘verify your details’.
- If you think your password has been compromised, contact the Service Desk, and change your password.
- Don’t use the same password for more than one account. Just don’t do it.
- Try and use a unique password with a mixture of letters, numbers and punctuation.
We do block most fake messages that are sent to your University email account, as we have ways of identifying them before they reach your Inbox. But some may still get through to you, unfortunately.