Posted by popular demand on behalf of Adele…
The TS Gateway service allows you to connect to your work PC from home or other off-campus locations, even when your work PC is on an internal University network (i.e. 10.x.x.x IP address). Used in conjunction with Wake On Lan. This gives you 24 hour access to your on-campus PC.
To use the service you must ensure that you have the latest Remote Desktop Client installed on the PC from which you are connecting back into work. If you are running Windows Vista or Windows 7, you should already have what you need. If you are running Windows XP or earlier, you may need to visit Microsoft.com and download a later RDP client.
Instructions
Prerequisite: the work PC must be set-up to allow Remote Desktop Connections and you will need to ensure that the ID that you are using is in the Remote Desktop Users group on the PC.
Launch Remote Desktop Client (you’ll find it by browsing to Accessories or just click Start…on Vista or Windows 7 (or Start.. Run if on XP) and type in mstsc and press Enter)
Click on Options as shown below:
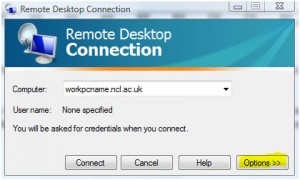
Click on Advanced and then Settings as shown below:
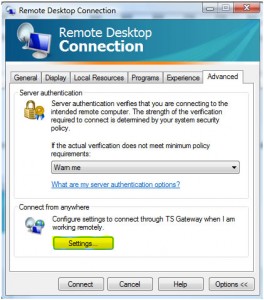
Complete the TS Gateway settings precisely as shown below:
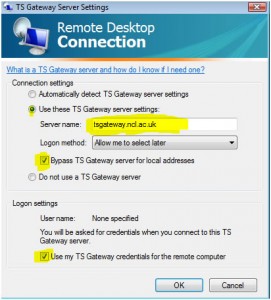
Click OK, and go back to the General tab. Enter the name of your work PC plus .ncl.ac.uk:
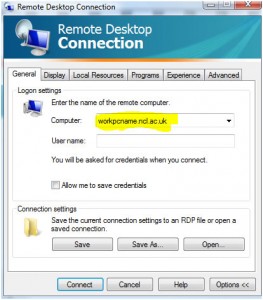
Click Connect. Enter an id that has rights to log on remotely to the PC. For example:
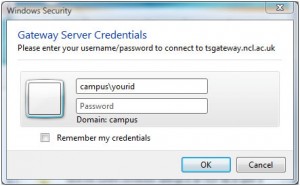
Click OK. (You can use a local ID, but you’ll need to qualify it by using machinename\ rather than campus\
Setting up a Vista or Windows 7 PC for remote access
Click Start…
Right-click Computer and then select Properties.
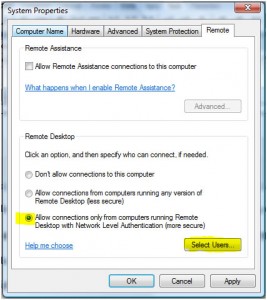
Click on Advanced system settings and, if prompted, supply the credentials of an account that has admin rights to the PC. Click on the Remote tab and Select Users:
Add the accounts for any user that you want to be able to remotely access the PC:
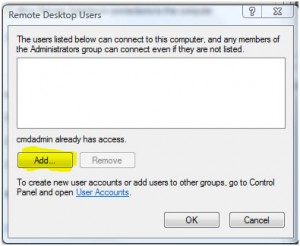
Then click OK… OK. All done.
You should test the settings from another on-campus machine before attempting to connect from off-campus.
The procedure is more or less the same for Windows XP but you will need to be logged on with admin rights before starting.
When using the above service, it is strongly recommended that you ensure your home PC is fully up-to-date with Windows Updates and is running good antivirus/antispyware software. Be sure to adhere to the University’s Computing Rules of Use at all times, and take care to protect sensitive and important data from unauthorised access as you would when working directly on-campus.










.gif)